Comprehensive security validation powered by a robust real-world attack library—delivering assurance and evaluating your true defense readiness.
ATLAS™
AI-Powered Security Validation
Stay Ahead of Attackers Before They Strike

Think Like an Attacker
Stay Ahead of Real-World Threats
Stop wondering ‘what if?’ and start knowing exactly how your security will perform when real threats strike.
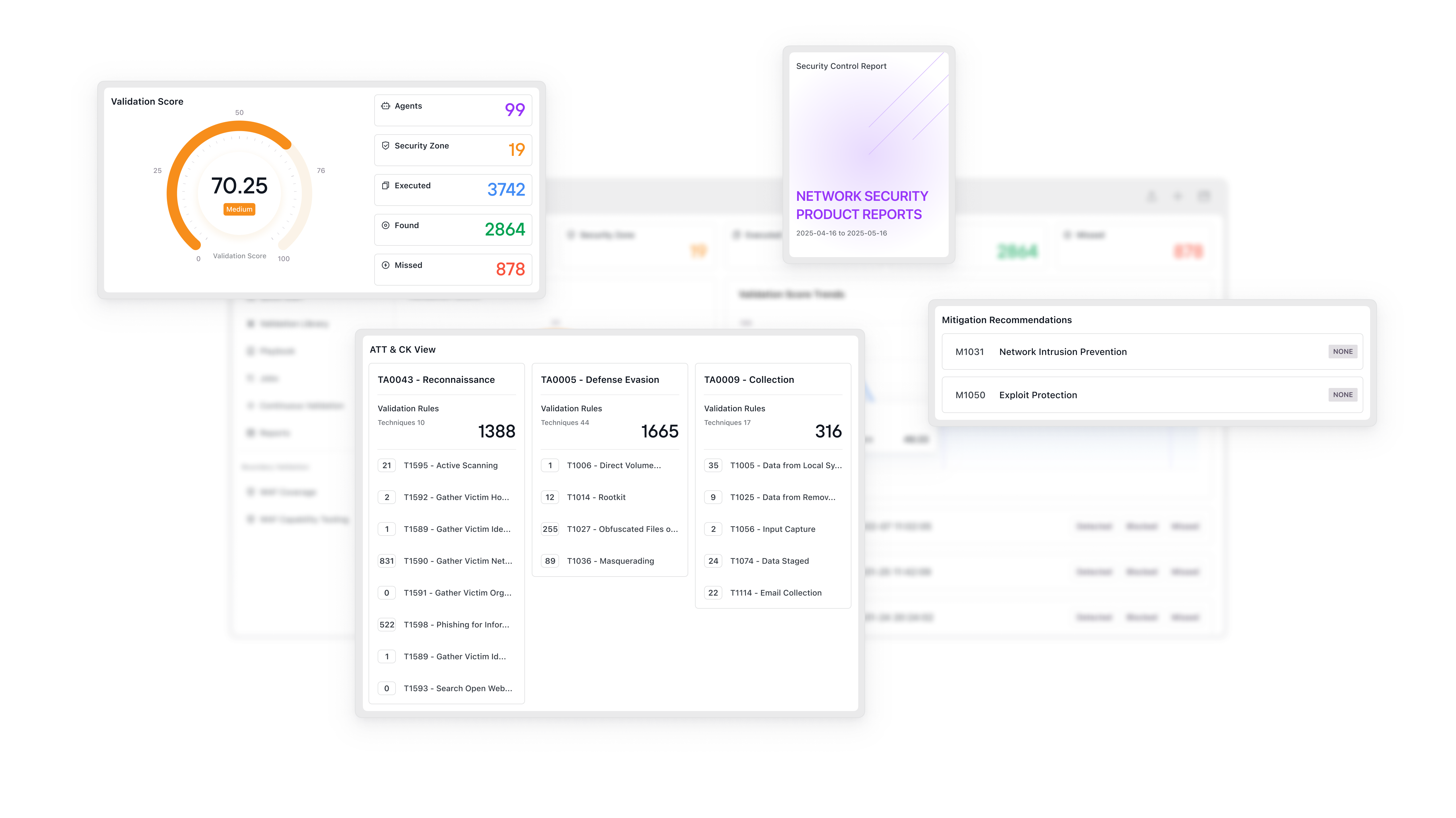
With ATLAS™ Security Validation, you gain:
AI-Powered Validation
Human-Level Understanding
When AI understands security like an expert. Validation becomes a conversation.
With TARA AI embedded in ATLAS, you gain:


From Insights to Action
Transform complex security data into clear decisions. No more guesswork, just data-driven security improvements with ATLAS™ Security Validation.
Transform Your Security Operations
Security Team
- Automate real-world attack simulations and boost validation efficiency by up to 90%.
- Replace slow, manual workflows with intelligent automation that delivers results in hours.
- Free your team to focus on closing gaps—not running tests.
SOC Team
- Reduce false positives by up to 75% through AI-powered security validation.
- Validate detection rules using real attack behavior, not assumptions.
- Let your analysts focus on real threats—not alert fatigue.
CISO
- Align security outcomes with business value through continuous, data-driven validation.
- Prove security readiness with insights mapped to MITRE ATT&CK and real-world threats.
- Move beyond dashboards—tell a compelling story at the boardroom table.
Blogs

Security departments are typically comprised of two core pillars: the Vulnerability Management…

Reporting security performance to the C-suite is perhaps the most daunting challenge…

Reflecting on security operations over the past two years, many cybersecurity professionals…